- +877 776 0673
- [email protected]
- Mon - Fri: 9:00 - 18:00 EST

Have you ever wondered how companies like Yahoo, Mariott, Equifax and Capital One get hacked and expose billions of sensitive user data?
Well, in the movies, the scene has a tech-savvy hacker who easily penetrates company firewalls, retrieves data, steals from the rich, and gives to the poor, all from a laptop while sitting in a local coffee shop.

Much of this is true. But the question remains, when and where did the hack begin?
It begins with you, an unsuspecting internet user, who is going about their typical everyday lives—surfing the web, checking social media, buying things online and responding to emails.
All the while, the hacker, let’s call them criminal, better yet, a cybercriminal, is collecting your personal and professional information without you knowing.
Phishing is a form of a cyberattack for cybercriminals to carry out and one of the easiest to fall for.
A successful phishing excursion can provide everything the hackers need to ransack their targets’ personal and professional accounts.
I often think that phishing is a professional sport played by cybercriminals, where their target is anyone who uses the internet to do everyday activities.
And the more they play and practice phishing, the more skillful they get.
Like fishing, the more often you cast your line, the better your odds of catching a fish.
Phishing is not the end of a hack unless you are the target.
Phishing is not the end of a hack unless you are the target.

It’s the start of the hack where the intended target is a wealthy multinational company.
As someone who enjoys fishing, I understand that if I want to catch a big fish, I will have to leverage a small fish as bait.
Yes, you are a small fish.
Phishing is a new kind of threat, OK kind of.
If you have been a netizen for over ten years, you may remember a Nigerian prince who was trying to transfer funds.
Please help me transfer millions of dollars?
This is a type of phishing strategy called a “fund transfer” fraud reaches victims by email.
Most of you reading this is thinking, “Edwin, I knew it was a scam.”
Great, but did you know that it’s one of the longest-running online scams which generates over $700,000 per year?
Phishing messages are always of an “urgent, private” nature.
Here is an example of a phishing attempt I recently received.
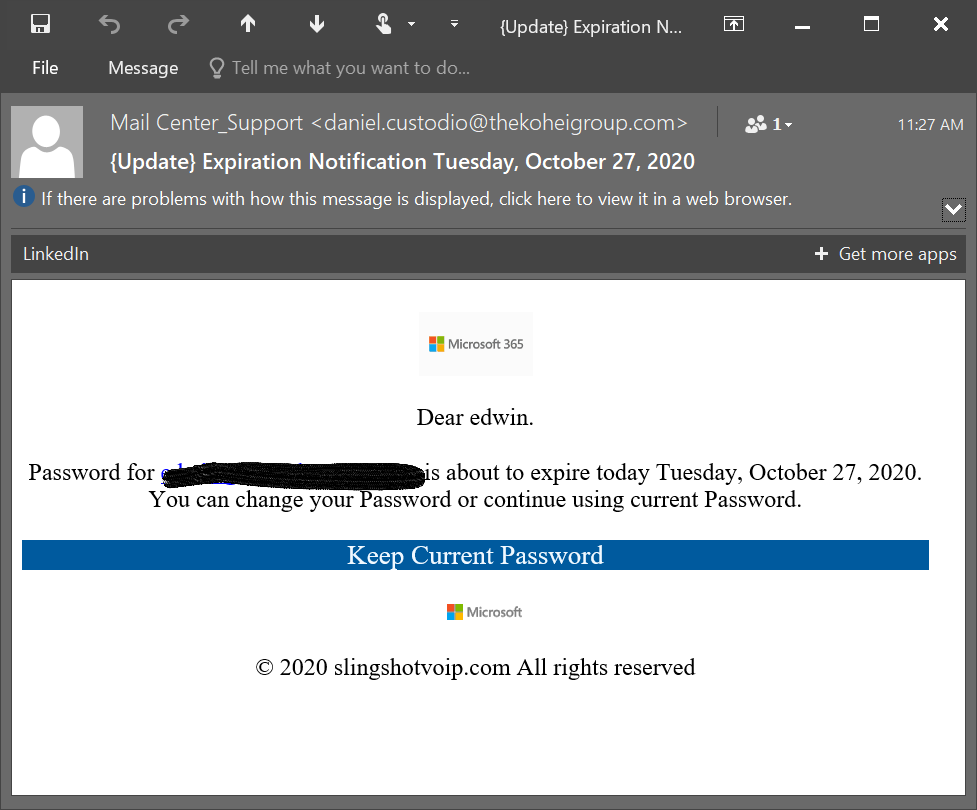
Typical data that hackers are looking to get during a phishing attack are:
The above email looks real, and if I were not privy to phishing attacks, I would click the link, verifying that I am a Microsft user, my email address and password.
I would’ve also given the hacker access to my email address where they could masquerade as me, emailing co-workers, clients, colleagues and friends.
To give you an idea of how widespread phishing is and how much companies stand to lose from a successful attack:
The average cost of a phishing attack to a mid-sized company is $1.6 million.
The best policy to protect yourself and your business from a phishing attack are to be vigilant, aware and suspicious of all emails. Be wary that hackers are relentless and are playing the numbers game, it could be not if you get hacked, when.
Suppose a phishing attack compromises your company. In that case, you have to be sure to have a business continuity plan(BCP) in place to recover to minimize the impact and get back to business.
The best policy to protect yourself and your business from a phishing attack are to be vigilant, aware and suspicious of all emails. Be wary that hackers are relentless and are playing the numbers game, it could be not if you get hacked, when.
Suppose a phishing attack compromises your company. In that case, you have to be sure to have a business continuity plan(BCP) in place to recover to minimize the impact and get back to business.
If you liked this article, be sure to read:
Please click Like if you found value in this article. Click Share to spread the love, thank you!