- +877 776 0673
- [email protected]
- Mon - Fri: 9:00 - 18:00 EST

As far as phishing tactics go, brand impersonation is the go-to strategy for hackers. Impersonating brands is a very effective way to phish for user emails and credentials from unsuspecting end-users.
And according to a recent analysis (October 2020), there are some pretty surprising discoveries about brand impersonation.
The top ten impersonated brands by their appearance in phishing attempts:
Web (43% of all phishing attacks)
Brand impersonation attacks come in three varieties:
Known brands
A known brand is where a well-known and trusted brand, like Google is impersonated.
Own-brand
Own-brand is where the company’s own name and branding are being used to attack it.
For example, a hacker using slingshotvoip.com to impersonate.
Related Stakeholders
Related stakeholder attacks use the brands of customers, suppliers, partners, and other organizations that work with the employees of the targeted company.
I recently received a phishing attempt from a hacker impersonating Microsoft.
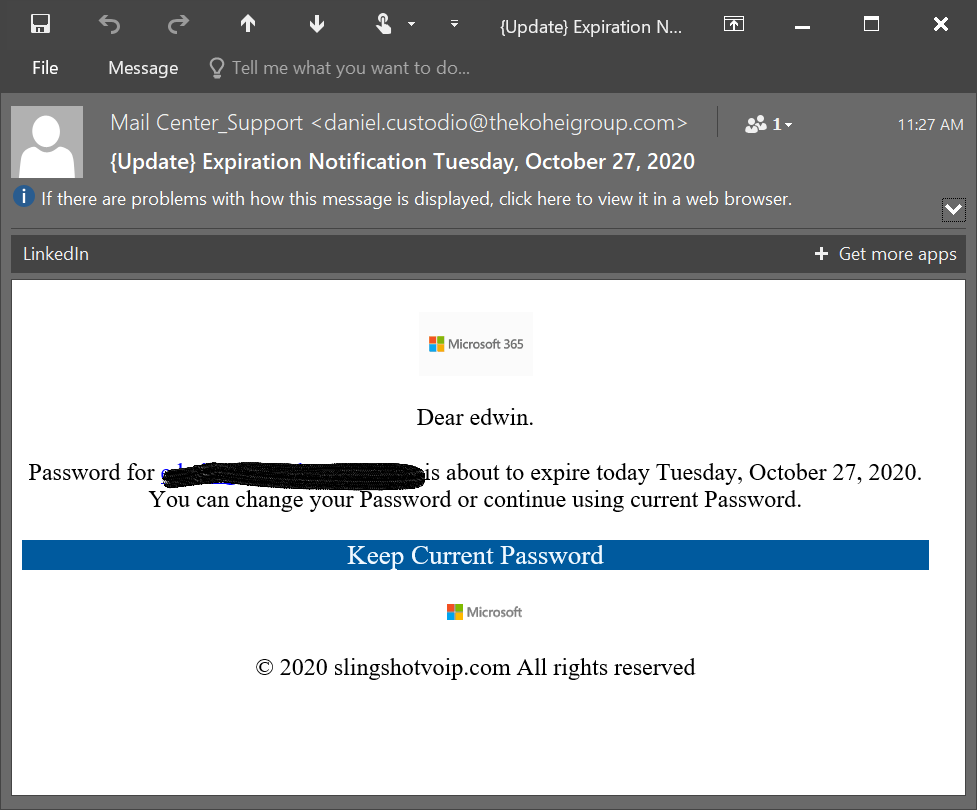
A couple of red flags:
Another recent phishing attempt that I received was from a financial institution in Canada.
In fact, it was a smishing attempt, a phishing attempt that leverages mobile text messages.
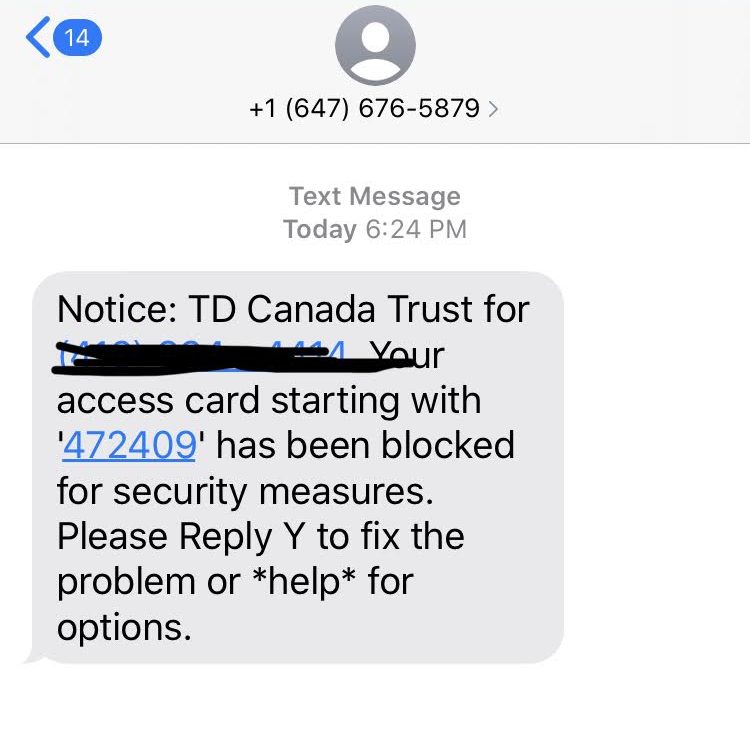
I’ll be honest with you, this one almost got me.
Having completed a recent transition on a TD account, I thought the message was legit.
The numbers they sent also matched the numbers on my access card.
Given the timing of the text message, I thought that there may be a small chance that this text could be real.
Rather than replying back via text message, I decided to call the phone number on the back of my back card.
The agent who answered told me it was not real and that they had many calls about it.
Quick Tips to Spot a Phishing Attempt
Hover over website addresses (URL) with your mouse, if the linked address is different from the text on the email, the message is fraudulent or malicious.
Hackers rely on the fact that unsuspecting users do not understand how domain names work.
For example, the root domain of this website is slingshotvoip.com, a real subdomain could be www.slingshotvoip.com or info.slingshotvoip.com.
slingshotvoip.com.phishers.com would be a subdomain of phishers.com and would not have originated from slingshotvoip.com because the reference to slingshotvoip.com is on the left side of the domain name.
I have seen this trick used countless times by phishers as a way of tricking users that a message came from a company like Microsoft or Apple.
Whenever a large company sends out a message on behalf of the company as a whole, the message is usually reviewed for spelling, grammar, and legality, among other things.
So if a message contains poor grammar or spelling mistakes, I’m willing to bet it didn’t come from a major corporation’s legal department.
No matter how official an email message might look, it’s always a bad sign if the message asks for personal information.
Your bank doesn’t need you to send it to your account number. It already knows what that is.
A reputable company should never send an email asking for your password, credit card number, or the answer to a security question.
There is an old saying that if something seems too good to be true, it probably is. That holds especially true for email messages. If you receive a message from someone unknown to you who is making big promises, the message is probably a scam.
I’ve received many email messages letting me know that I had won the lottery. The only problem is that I don’t play the lottery.
If you get a message informing you that you have won a contest you did not enter, you can bet that the message is a scam.
Depending on how far down you’ve communicated with the phisher, sooner or later, they will ask for money. They will ask to cover expenses, taxes, fees, or something similar. If that happens, you can bet that it’s a scam.
If you have been a netizen for over ten years, you may remember the Nigerian prince who had the challenge of transferring their funds.
Phishers who want to use intimidation don’t always pose as a bank. Sometimes they’ll send messages claiming to have come from a law enforcement agency, the IRS, CRA, the FBI, or about any other entity that might scare the average law-abiding citizen.
In Las Vegas, casinos look for anything that doesn’t look right (JDLR), as they call it.
The idea is that if something looks off, there’s a good reason why. This same principle almost always applies to email messages.
If you receive a message that seems suspicious, it’s usually in your best interest to avoid acting on the message.
The bottom line, if you want to stop brand impersonation phishing attacks, be prepared to identify all three types of attacks. Unfortunately, these types of attacks are on the rise.
It’s not realistic to expect everyone, including yourself, to spot all three types of brand impersonation attacks. When all three tactics are taken into account, there are too many brands and too many phishing tactics for busy employees to spot them all.
It only takes one to get through to compromise your entire organization.
References:
https://www.checkpoint.com/press/2020/microsoft-is-most-imitated-brand-for-phishing-attempts-in-q3-2020/
If you liked this article, be sure to read:
Please click Like if you found value in this article. Click Share to spread the love, thank you!